Securing Sensitive Configuration properties with Jasypt in SpringBoot
Securing Sensitive Configuration properties with Jasypt in SpringBoot
Spring Boot is a popular java application development framework. To make your application to be production ready, we need to ensure that application properties that are stored in `application.yml` or `application.properties` are not stored in plain text.
Some of the configuration data may contain sensitive information such as:
- API Keys
- Database connection properties ie username, passwords.
It is therefore critical that these information is kept safe by maskin or encryption.
Jasypt (Java Simplified Encryption)
This is a java library that allows the developer to add basic encryption capabilities to their project with minimum effort and without the need to have a deeper understanding of how cryptogaphy works.
Benefits of having Jasypt integrated with SpringBoot
- It Ensures sensitive data remains confidential even if the configuration file is compromised.
- It secures sensitive information in configuration files.
- Implement seamless decryption mechanism during application startup without changing the existing codebase significantly.
Steps to add in your spring boot application:
a) Add jasypt dependency to your spring boot project
maven users
<dependency>
<groupId>com.github.ulisesbocchio</groupId>
<artifactId>jasypt-spring-boot-starter</artifactId>
<version>3.0.5</version>
</dependency>gradle users
implementation 'com.github.ulisesbocchio:jasypt-spring-boot-starter:3.0.5'Once this is added, the project is ready to encrypt sensitive data.
Next we’re going to encrypt some of the sensitive properties like below:
order.securekey1=somesecurevalue1
order.securekey2=somesecurevalue2We want to ensure that the values somesecurevalue1 and somesecurevalue2. are encrypted.
Encypting the values
We have two options for encrypting our values.
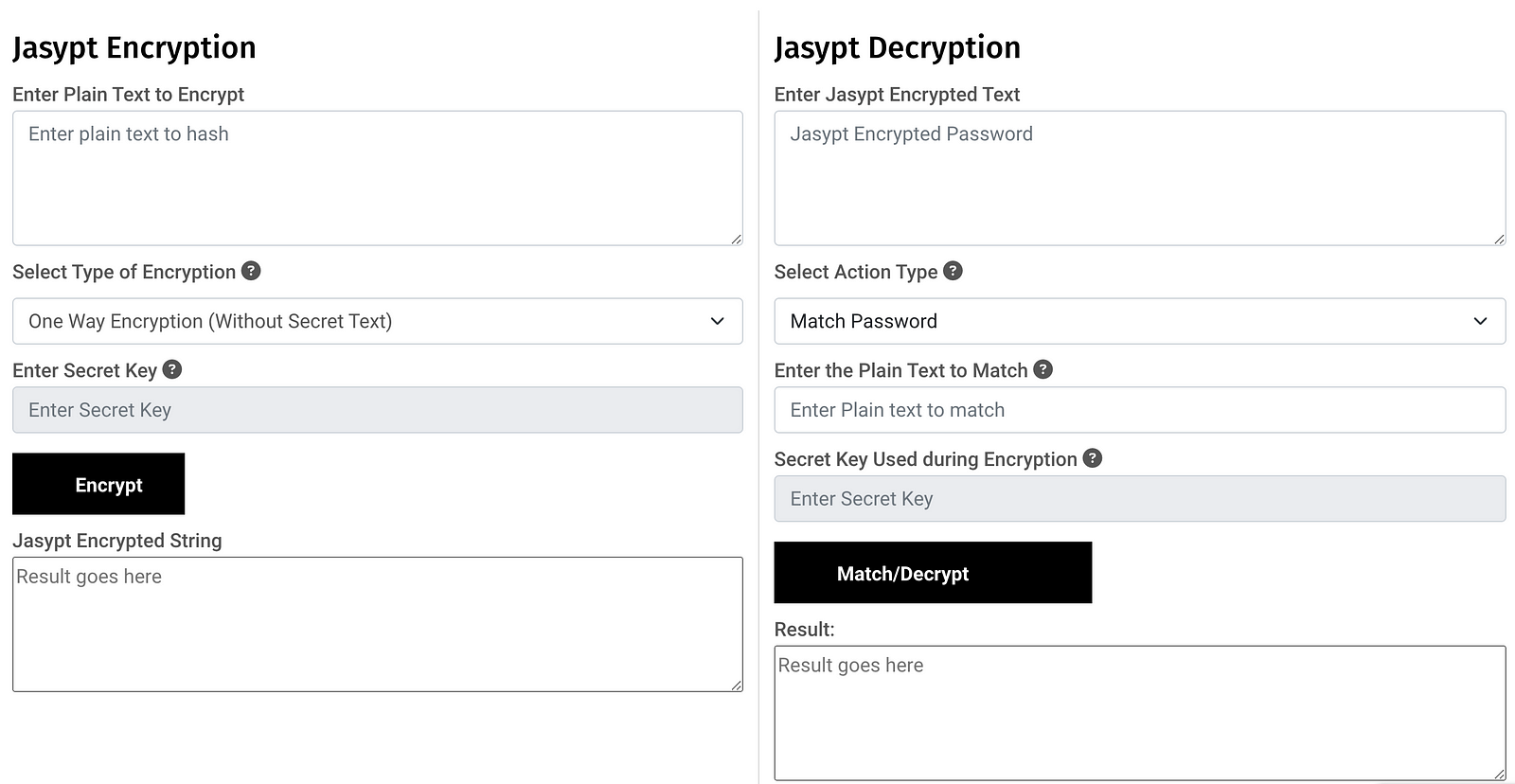
a) Use an online tool
Jasypt Encryption and Decryption Online
Jasypt online free tool for encryption and decryption.This tool supports one way and two way password encryptor using…www.devglan.com
b) use Jasypt library jar
Download the latest versionhere https://mvnrepository.com/artifact/org.jasypt/jasypt
run the command
java -cp jasypt-1.9.3.jar org.jasypt.intf.cli.JasyptPBEStringEncryptionCLI input="somesecurevalue1" password="Ymw54674&*Kms" algorithm=PBEWithMD5AndDES
output

NOTE: we need to also add an encryption key in our properties file so that Jasypt know how to decrypt these values. ie Ymw54674&*Kms specified in the above command. This key can be stored in the applicaton.properties or as an environment variable.
so now our properties file will have the below updated configuration.
order.securekey1=ENC(5Gn91Do/JgmehGnCeFhKoIyf2hGf1Ae44ikoeuXOVeY=)
order.securekey2=ENC(uio1wUOTcsDDojDulOJ/Ki4ayNz3hVASLkTE4cJf2pI=)
jasypt.encryptor.password=Ymw54674&*Kms
To have more control over the encryption process, Jasypt offers several configuration options eg changing the encryption algorithm, adjusting key obtention iterations.
With advanced configurations options the properties file is updated as below.
order.securekey1=ENC(5Gn91Do/JgmehGnCeFhKoIyf2hGf1Ae44ikoeuXOVeY=)
order.securekey2=ENC(uio1wUOTcsDDojDulOJ/Ki4ayNz3hVASLkTE4cJf2pI=)
jasypt.encryptor.password=Ymw54674&*Kms
jasypt.encryptor.algorithm=PBEWithMD5AndTripleDES
jasypt.encryptor.key-obtention-iterations=1000
jasypt.encryptor.salt-generator-classname=org.jasypt.salt.RandomSaltGeneratorTesting the integration
To make sure our application works as expected we will define a test function to output the decrypted properties.
@Autowired
private Environment environment;
@Test
public void testDecryption() {
String decryptedPassword = environment.getProperty("order.securekey1");
assertEquals("somesecurevalue1", decryptedPassword);
}To run the tests, run below command
./gradlew clean test --info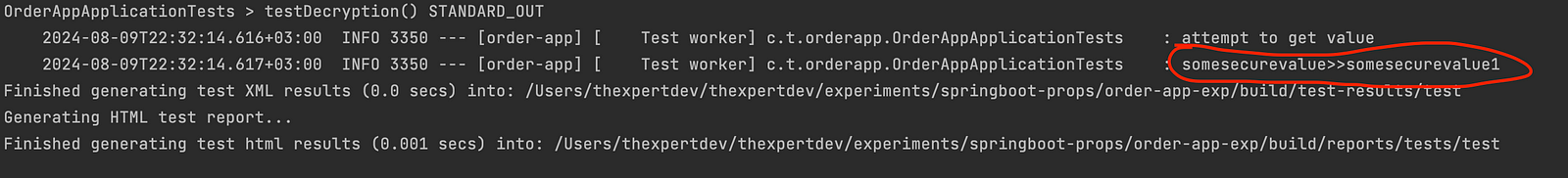
Integrating Jasypt with your Spring Boot application is a straightforward way to secure sensitive information in your configuration files.
By following the steps outlined in this guide, you can ensure that your application properties are encrypted and protected, reducing the risk of exposing critical data.
Update
If you get the below error
java.lang.IllegalStateException at DefaultCacheAwareContextLoaderDelegate.java:180
Caused by: org.springframework.beans.factory.UnsatisfiedDependencyException at ConstructorResolver.java:795
Caused by: org.springframework.boot.context.properties.ConfigurationPropertiesBindException at ConfigurationPropertiesBindingPostProcessor.java:99
Caused by: org.springframework.boot.context.properties.bind.BindException at Binder.java:391
Caused by: com.ulisesbocchio.jasyptspringboot.exception.DecryptionException at DefaultPropertyResolver.java:63
Caused by: org.jasypt.exceptions.EncryptionOperationNotPossibleException at StandardPBEByteEncryptor.java:1165Use below Fix
Add @EnableEncryptableProperties to all application classes (classes with @SpringBootApplication).